Identity and Access Management(IAM) is one of the most tedious and risky tasks in application development. However these days, not everything has to be built from scratch. You can outsource risky tasks like identity authentication to third-party applications. In this article, I will list why you need to avoid storing passwords while enhancing the security of your application.
What is Identity and Access Management(IAM)
IAM is a framework of policies, processes, and technologies that enable organizations to manage identities and control access to applications. IAM can be broken down as follows:

Authentication is the process to validate the user’s identity, this is done by verifying the user-provided credentials. Most commonly these are username/email and passwords. Additional authentication factors can be added for more security like the on One-Time pin via SMS/Email, Authentication apps, and Biometrics.
Authorization is the process of provisioning and controlling user access. Ensuring that the user can only access or perform tasks that they are authorized to. This process follows after the user has been authenticated into the application. To better manage the authorizations process, access to resources/tasks are grouped in buckets referred to as entitlements or roles. Access provisioning is easier as the user profiles are assigned one of these “buckets”. While the app can easily validate that the task being performed is indeed in the “bucket” assigned to the user.
Access Reviews is the process of regularly reviewing the access granted to users. Reviews are performed against standards and policies, e.g. Users that have not logged in 3 months need to have their access disabled. Access Reviews are more common internal enterprise applications rather than public applications with self-service sign-up.
How Authentication Works
Authentication has the most risk as it requires the storing and verification of user credentials. Most people reuse the passwords on multiple platforms for convenience. This means that your application contains an email/password combination that can be used to access other platforms like online banking. Passwords are not stored in plaintext but a hashed/encrypted password is saved. A one-way hash function like MD5 and SHA1 is used to ensure that passwords cannot be reversed engineered. Every time the user logins, the hash function is applied to the provided password. The output is compared to the password hash against the user profile in the database.
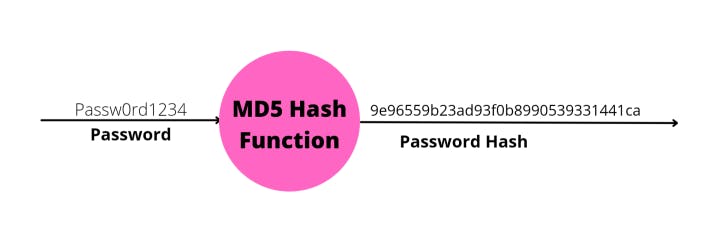
This is not secure as vulnerabilities have been identified on one-way hash functions like MD5(used by WordPress) in recent years. The worst vulnerability is a collision attack, where two phases produce the same hash output. These do have workarounds but keeping up and mitigating against these vulnerabilities requires a lot of effort and only excites security experts. The alternative is avoiding the storing of passwords and relying on a trusted third party to validate user identity.
Why Outsource Authentication.
- Security: Keeping passwords secure task a lot of effort that does not add value to your applications. Third-party identity managers like Google, Microsoft, and LinkedIn have dedicated security experts behind their Identity Authentication services. Vulnerability is addressed within hours of being identified.
- User Experience: Delegating the user authentication may improve user application as the Identity Managers like Google offer a “one-click” authentication, this way your users can avoid filling out forms. e.g User who navigated from Gmail or other Google products will be presented with the “Continue with Google” option required to authenticate on your application. This also promotes user conversion on your application as users are not promoted with forms when clicking on links on your newsletter.
- Data Quality: Users have one less profile to manage, user information is sourced from the identity manager. e.g. profile picture. As a result, the information provided will be of quality because users only need to update information in one place. The alternative has users creating “dummy/fake” accounts just to access the application. Internal enterprise applications can have a single source of the user profile like Azure Active Directory. This provides global control of the profile across all applications. People that have left the employ of the company can have their profile deactivated in one place.
Thank you for reading, I hope this clarified a few things on Identity and Access Management.
Originally published at loggedon.co.za on March 12, 2022.

